How do you know your if your IT providers are maximising your Information Technology potential?

10 minute read | 25 minute process | Author: Glenn Thow, CEO, LCS Group
To get yourself in the correct mindset, ask yourself these two questions (or jump straight to our 5 tips):
Q: Do you know how well your IT system is configured and performs compared to what is possible?
Q: Is IT adding value to your business to its fullest potential or just another money draining cost?
A: Well from our experience of helping companies with their IT needs & problems over the last 25 years, I would say that a significant proportion of SMB business owners don’t really know for sure. Most companies simply accept what their IT advisors tell them and why wouldn’t they? They believe their GP when given a diagnosis, their accountants when receiving tax advice and their lawyers when they have a legal issue.
The only difference is that in our industry to be an IT consultant you just need to have more knowledge than the person you are talking to, and your deemed as a specialist. You don’t need to have completed years of education, pass lots of stringent exams and be subjected to ongoing legislative professional scrutiny to start an IT business.
As a result, many organisations have never enjoyed high levels of IT performance, they have no benchmark of comparison and therefore are more inclined to believe the explanations and potential excuses of their advisors and accept what they have as being optimal.
Q: Everyone has IT problems right, that’s why every business needs some form of IT support?
A: Whilst an IT system requires ongoing maintenance and management and users often need support, underperformance & unreliability should not be acceptable.
 IT support and management should be a pro-active service that adds value to a business by keeping its systems operating at maximum levels of performance, reliability and security. It should provide its users with tools that enhance their levels of productivity and efficiency in turn delivering high levels of service and satisfaction for its customers. IT should be viewed as an investment not a cost, add value across the business and have tangible returns on the bottom line. It should not be a never-ending cycle of reactive break fix scenarios for which businesses pay a premium and then do not enjoy the rewards of their IT investments to its fullest potential.
IT support and management should be a pro-active service that adds value to a business by keeping its systems operating at maximum levels of performance, reliability and security. It should provide its users with tools that enhance their levels of productivity and efficiency in turn delivering high levels of service and satisfaction for its customers. IT should be viewed as an investment not a cost, add value across the business and have tangible returns on the bottom line. It should not be a never-ending cycle of reactive break fix scenarios for which businesses pay a premium and then do not enjoy the rewards of their IT investments to its fullest potential.
The only way to really know if your business is making the most from technology is to ask your IT advisors for a detailed honest review of your system status, its value, risks and opportunities. However, there is always the risk with this that they might not be totally transparent or indeed in some cases know how to truly optimise a system by believing their methodology is the best option for you. People simply don’t know what they don’t know and that’s a fact in all walks of life and business. It is impossible to tell someone else about something you are unaware of, and human nature to defend your corner and opinions, especially if you are working in the capacity of a professional advisor.
Better still get an unbiased opinion from a third party, most IT service providers at the top of their game provide a full detailed analysis of all aspects of a system before giving any advice. The most competent and confident of these providers would likely do this for free as they know there is a high chance of engaging with the client by the added value they will bring to the table as a result of their knowledge and expertise.
Whilst it is impossible to know the true big picture of how your well IT compares to what is possible, the following tips will provide you somewhat of an insight. If some of the fundamentals are not in place then there is a strong likelihood that some of the more important and complex elements of a system implementation may also be missing.
Tip 1: How does your network look physically?
Take a look at this before and after of a customer who sought our help with network performance and reliability after losing faith in their existing provider.
A pretty good indicator is the physical state of your network, especially your servers, switches, routers, firewalls, cabling and other ancillary equipment. If your IT system resembles the picture on the left above, then your IT providers are not only doing you, but also themselves a dis-service. Not only is this unsightly, it is also more prone to failure, more difficult to troubleshoot and any fixes are likely to take longer to rectify which in turn usually results in higher costs.
Based upon the premise that IT providers should be looking to optimise performance, minimise failure and security risk for their customers it does not seem sensible to not be professionally pro-active with this IT implementation fundamental.
Tip 2: Your desktops can be an insight to what you cannot see behind the scenes.


A system without a clear and consistent desktop group policy that does not give users a unified experience with and level of configuration consistency across the business is always going to lead to some level of negative compromise. If you see random wallpapers, application icons, files, folders and shortcuts on users’ desktops it points to a system that is likely not optimised and not well put together.
Systems configured in this way are difficult to manage, have a higher risk of security implications and often perform lower than their potential. It is also likely that much, if not all of that desktop data is not backed up and may point to a similar haphazard configuration behind the scenes in the core of the network.
Tip 3: Do your users have Admin rights?
Probably one of the most important things to check is that if any of your users have Administrator rights over their desktop or the network as a whole.
A user with admin rights is simply running on a security knife edge! It opens up a world of opportunity for cyber criminals to lure your users into installing code that has malicious intent, whereas without Admin rights this could be prevented. It also acts as a barrier against users independently installing applications or services without proper controls that could negatively impact your system.
Restriction of Admin rights is one of the key recommendations for the Governments Cyber Essential program see further information here. A person who configures a system granting day to day users Admin rights is either, naïve, stupid or ignorant of the significant risks.
To find out if a user has Admin rights follow these simple steps in Windows 10:
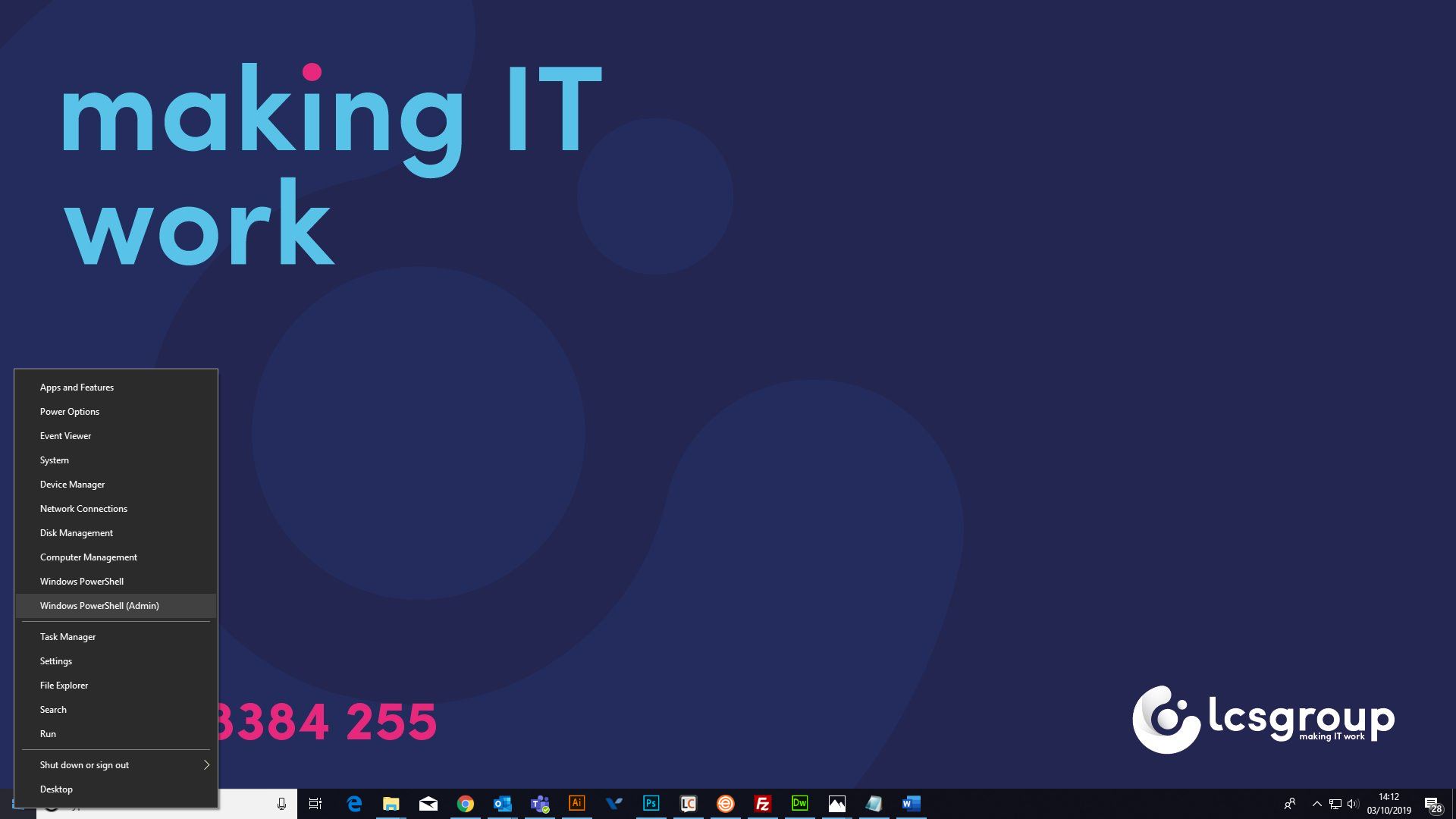
At the prompt in the blue window type exactly net localgroup administrators and press the enter key on your keyboard. The results are displayed it will show you who has administrator rights.
If the user’s login name appears in the list or it says “Domain Users” then it indicates Admin rights are active for that user and the latter for all users. In either case you should ask your IT advisors to change this immediately.
In the example above the users listed on my PC are valid administrators and our support team and as they only log in with these accounts when necessary, this is the safe and recommended option.
You can see my username glenn.thow does not appear in the list as when I login I do not have these Admin rights to protect me, my PC and our wider network.
This is such an important setting that if in any doubt check with your IT advisors as soon as possible.
Tip 4: Windows updates
Ensuring that your system is configured to receive and deploy Windows updates, patches and fixes is absolutely essential. Not only will these update fix issues with your PC and associated Microsoft Software and Edge Browser, they will also protect you from malicious attack by deploying updates that protect you from security vulnerabilities.
Simply type exactly Windows Updates into the Widows 10 search box and press the enter key on your keyboard.
This screen will tell you if your system is up to date and when it was last checked.
You can also check further by clicking “View update history”. If your system says it is not up to date or you do not have any updates showing in your history within the last two to four weeks then this would raise a red flag and you should question your IT advisors.
We do not recommend you attempt any updates until you have consulted with your IT providers as some may take considerable time and potentially disrupt your applications.
A well manged IT system is configured to deploy Windows updates regularly and in a controlled manner by your support team and if this is not the case then it may be time to ask some questions.
Tip 5: Windows security
Just like checking your Windows updates checking the security status of your PC is the same simple process.
Just type exactly windows defender security centre into the Windows 10 search box adjacent to the start button and press the enter key on your keyboard.
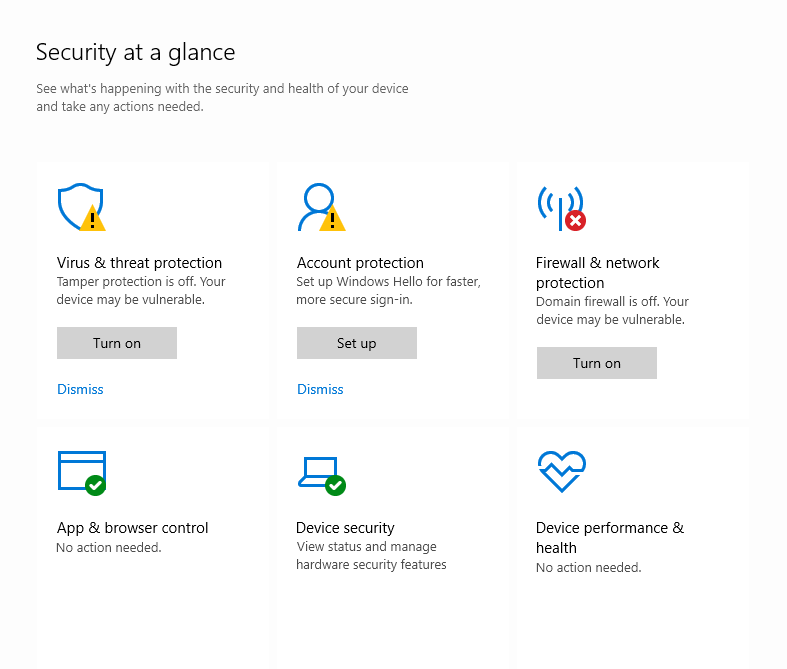
To interpret the results displayed use the following guidelines:
Green: This element is active configured correctly and confirms to Microsoft recommendations and indicates no risk.
Amber: This element is not active or configured but may not be an issue or risk. E.G it may indicate that OneDrive is not setup, or the user is not using a 4 digit PIN for login security. However, it may be worth checking if some of these features could add value if optimised.
Red: Indicates that there is something not configured correctly or switched on and likely poses a risk to the system. Any red symbols should be discussed with your IT advisors for peace of mind as soon as possible.
In summary
The above tips are merely to give you an indication of how well some of the basics are implemented and managed within your IT system. That said they are an excellent indicator to the potential state of the whole network, where significant risk or potential may lie.
I find it incredible that when a new client comes to us with a specific problem and we carry out a full IT review just how much we unearth that they were unaware of, and why would they be, they rely on the advice of others that know more than them!
Who knows if you your system has the potential to drive like Ferrari but runs like a milk float or poses unnecessary risks and vulnerabilities?
Maybe it’s time to find out and question your IT advisors or seek independent advice, it could be a move that adds value to your business, users, customers and most importantly your bank balance!