2 minute read | Cyberwatch-001: Microsoft 365 2FA Attack | Author: Ryan Gambrill
Protect yourself and your business from the latest Microsoft 365 attack.
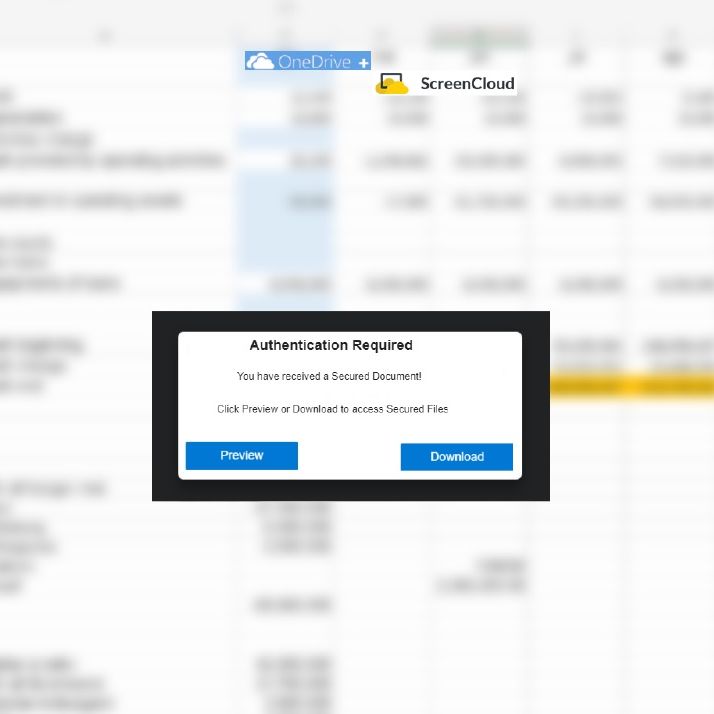
Cyber criminals have devised a method to acquire your Microsoft 365 login details and cleverly obtain your two-factor authentication (2FA) code that is sent to your mobile phone.
Behind the scenes, the bogus webpage is capturing the login information and attempting to log in using the credentials you have provided in real-time. As this all happens real-time, you receive your genuine Microsoft 2FA code at a time that doesn’t appear out of the ordinary and share this with the cyber criminals instantly by entering it into their bogus webpage. Following this process, the cyber criminal will have gained access to your account and you have been compromised.
If you do receive any of these types of email from someone you recognise, i.e. a contact, customer or supplier it would be wise to contact them and let them know as it is likely they have already been compromised to get your email address.
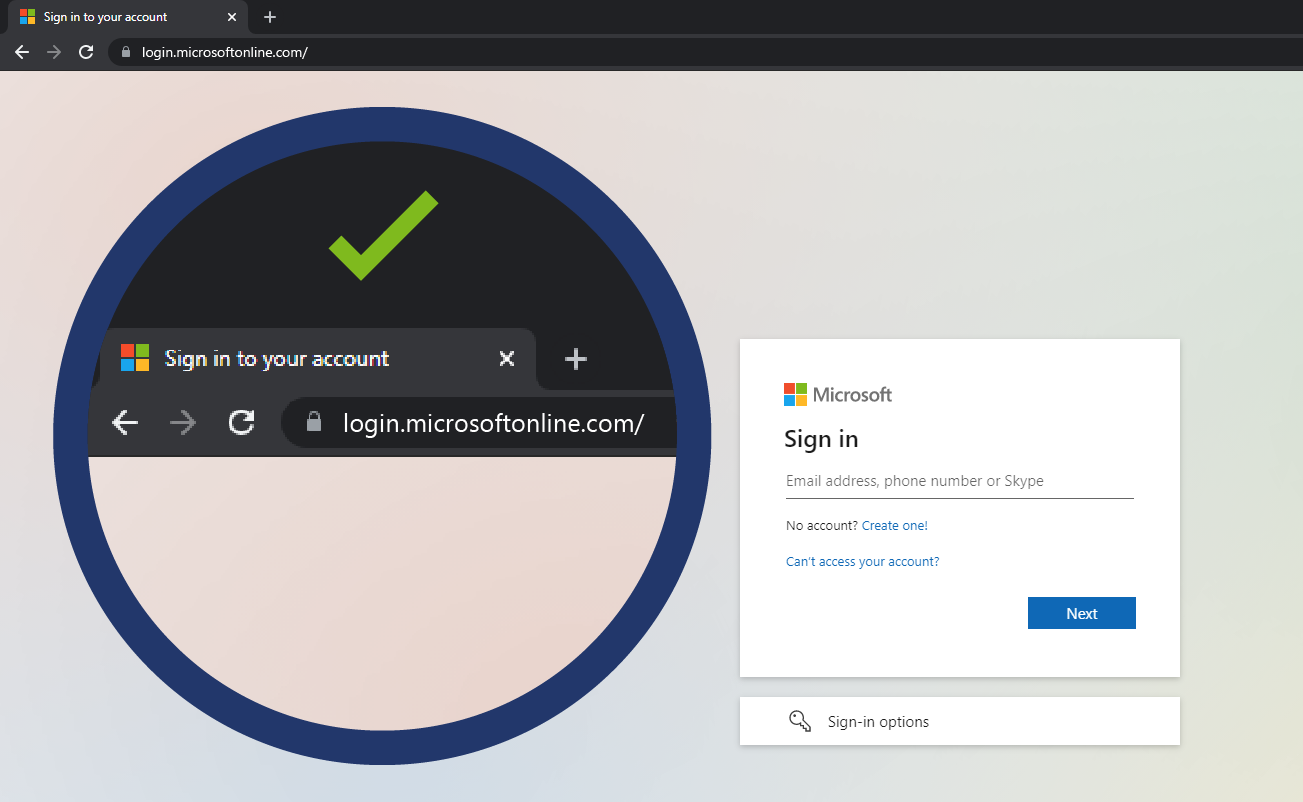
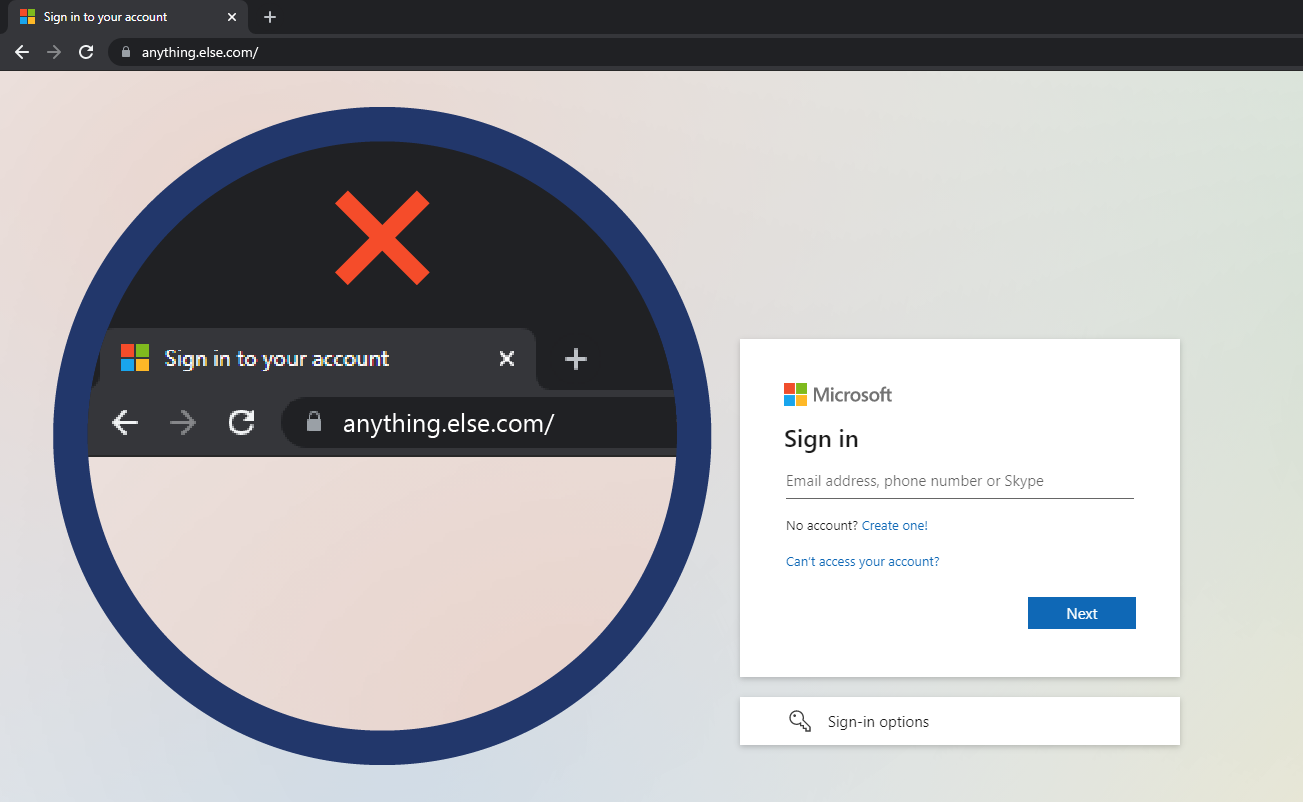
Remember to always check that when entering your Microsoft credentials, you only do so on the website address https://login.microsoftonline.com/. See how this attack in particular differs from that and how easy it would be to avoid the attack with extra care and vigilance.
Safe Site Example:
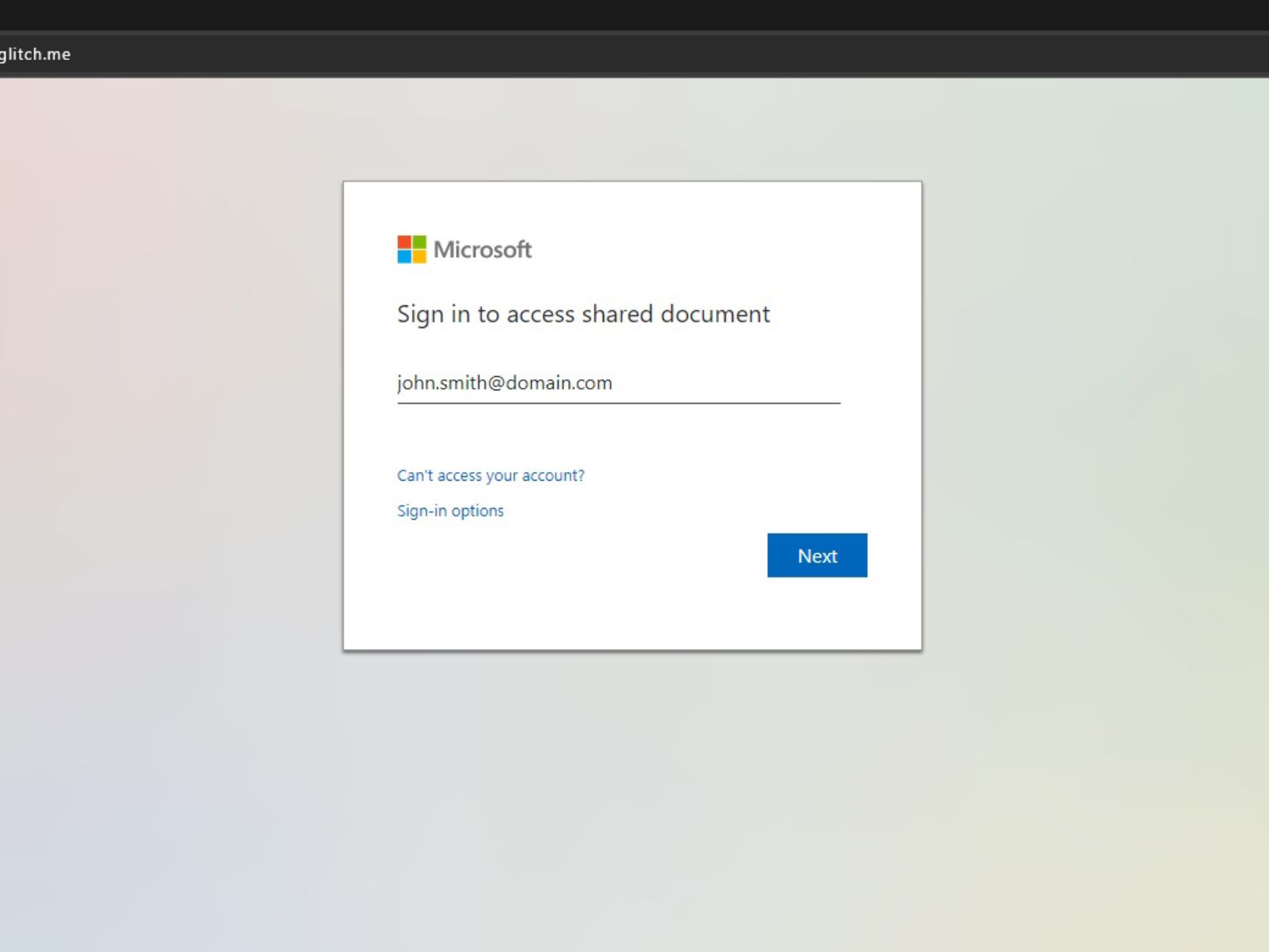
Dangerous Site Example:
In Summary
Whilst Microsoft 365 itself is very secure, and Two-Factor / Multi-Factor Authentication is an added layer of effective protection in preventing cyber-criminals from accessing Microsoft 365 accounts, the most powerful tool is a vigilant end-user.
In this scenario especially, its vital to understand that at no point has any part of the system been ‘hacked’. Instead, the user has been Socially Engineered (tricked) into willingly parting with their sensitive login information. There are no levels of practical security that can defend against sharing your information with a cyber criminal, and it is comparable to handing your front door key over to a burglar before leaving the house.