How does Multi-Factor Authentication work and how does it protect you?

5 minute read | Author: Glenn Thow, CEO, LCS Group
The landscape of cyber-crime is changing, no longer are the criminals seeking to access your data merely by ‘hacking’ into systems, they are now looking to exploit the weak link in the chain which is you (the user)!
With modern well put together IT platforms now boasting a host of physical barriers, such as sophisticated firewalls, malware detection and prevention tools, the fraudsters are preying on the human side of the equation more than ever before.
One of the most common forms of attack is to try and get access to your Office 365, Azure or VPN username and password. They do this commonly by creating bogus email or instant messages directing you to a web page to verify your credentials and capture them for their own use.
The scary thing about this process is that usually nothing actually happens right away for they have teams of people that probe your emails and data to gain an understanding of who you are communicating with and then create often quite sophisticated scams once they see an opportunity.
This can often take days, weeks or even months for them to formulate a plan where they have the very best chance of success.
In one of its simplest forms, and by way of an example they will monitor the emails for a company director and see how he issues instructions for his accounts team to make payments to suppliers.
The criminal will then issue an instruction to make a payment to a bank account by creating a fictious story and of course then transfer those funds quickly and steal the proceeds.
Remember the cyber criminal has had full access to that directors’ email for some time, knows who he or she is talking to and what about. They also see all of their appointments, know when they are in meetings, out of the office or even on holiday.
Its also common for the criminal to infiltrate conversations and pose as the person they’ve hijacked. In this way they can have conversations with third parties and redirect any replies so the owner of the inbox is unaware what is taking place.
What is Multi-Factor Authentication?
 Like the name suggests it is a mechanism that requires multiple forms of authentication to gain access to an account or system, above and beyond just the username and password.
Like the name suggests it is a mechanism that requires multiple forms of authentication to gain access to an account or system, above and beyond just the username and password.
This can be in a few varying forms:
- Fingerprint or face scan
- An authentication app on your mobile device
- Text message to your smartphone
- Telephone call to a nominated number
- A card reader device (most commonly used by banks)
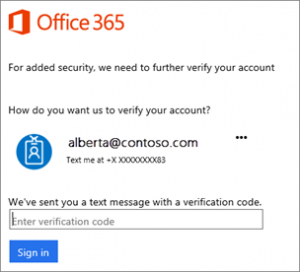
From a Microsoft Office 365 perspective the most common options are a text message or authenticator app on a smartphone.
You may already be familiar with this process for web logins such as Paypal, your bank and other sites where financial transactions take place. However, it is not limited to only money related sites, the perpetrators are equally keen to access your social media accounts, even if its just to build up a better profile of you to make the ultimate scam more believable.
The bottom line is that as humans we are more likely to trust the people we know personally and care about and this is positive side of our perception can be exploited as a weakness by the criminals.
So with Multi Factor Authentication in place not only will it prevent a criminal gaining access to your account but it will also alert you that someone is trying to do so immediately by you receiving the request to authenticate, allowing you time to notify your systems administrators and get your password changed.
How easy is it to implement?
Well that’s the great part, not only is it simple to install and setup from your Office 365 administrator portal, it’s also a free part of your Office 365 subscription so there is absolutely no cost to implement this essential feature.
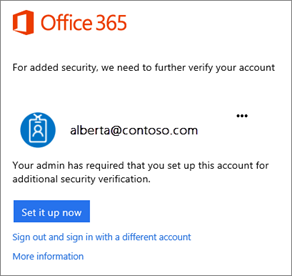
Once the feature has been switched on in the Office 365 portal the end user will be prompted to setup their preferred authentication method and enter their mobile phone number if text or call option is chosen.
In addition, this process also allows the end user to setup automatically generated passwords for offline versions of applications like Outlook for example.
If MFA is being deployed to a number of users by an IT department then it is important to notify them in advance and preferably provide them with a step by step guide or video to help them make the right choices.
There is a good chance that if you do not do this that some end users will simply call the help desk and report the issue or seek guidance, wasting time and potentially confusing the issue.

In Summary
Multi Factor Authentication is free simple to deploy and provides a strong layer of protection against allowing criminals to access your Office 365 account with a notification if they do and try to login.
Bearing this in mind it really is a nor brainer and you should ask your IT providers to deploy it as soon as possible.
It may also be worthwhile considering utilising this technology in conjunction with Office 365 Advance Threat Protection (ATP) to eliminate the Phishing emails before they even hit your inbox. For more information on ATP and its benefits, check out our blog here.