2 minute watch | Cyberwatch-003: Microsoft Office Document Exploit | Author: Glenn Thow
Defend against malicious macros in Microsoft Office documents.
Recently, Microsoft patched a security vulnerability within their Windows operating system. The vulnerability gave cyber criminals the ability to craft malicious Microsoft Office documents via a remote code execution. In simple terms this means that they can embed malicious scripts that can potentially attack your system when you open these documents, Word, Excel, PowerPoint etc.
Preventing Such Attacks
Rest assured; LCS deploy these updates to your devices daily so you can keep peace of mind knowing that we are keeping you up to date with all the latest security patches. These include updates not only for Windows, but for the anti-virus software that we deploy to your devices.
Combined with keeping on top of updates, the fact that your user accounts do not have elevated permissions provides a strong security barrier: if your device was to become compromised, the attacker would unlikely be able to immediately cause any detriment to your system due to your account not having administration rights.
However, it is always very important to understand how to spot a malicious Office document. An Office document (Word, Excel, etc.) is a very easy way for cyber criminals to hide detrimental code (referred to as a macro) that could release itself onto your system if opened, and deploy ransomware, malware and viruses.
Understanding How The Attack Works
There are already security measures in place that warn you if a document may contain malicious code. For example, if you open an Office file containing a macro or other active content, you will see the message below:
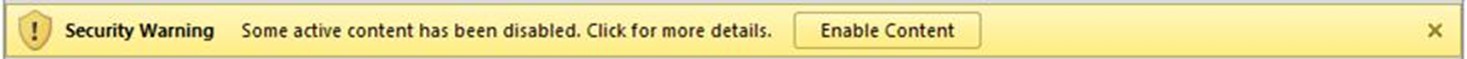
Do not click “Enable Content” unless you are 100% certain (perhaps you are expecting a macro’d document from a colleague) and that there is no way this document could have been compromised.
It is important to be particularly cautious if the document was emailed to you from an external party especially if you are not expecting a document from them. It would be good practice to check with them before enabling the content.
Remember the person who sent you the document even if you know them, may have had their account compromised so if you are suspicious contact them by phone rather than email.
It is important to be particularly cautious if the document was emailed to you from an external source and if you are not expecting a document from someone you know it would be good practice to check with them. Remember the person who sent you the document may have had their account compromised so if you are suspicious contact them by phone rather than email.
In Summary
Microsoft Office apps come with a feature called “Trust Center” that provides defenses to what could potentially be malicious code. The Trust Center is enabled by default as part of the LCS deployment policies.
Another good practice is to ensure you turn off or reboot your device regularly, at least daily to ensure that any security updates we deploy for you are fully activated.
As with potential cyber threats, prevention and knowledge is our best defence .